11.1 General Page
This is where the location of the trusted root container is specified for the proxy to read and copy the certificates listed in this container. For example, if you are using LDAP to secure the authentication profile, the trusted root certificate (which was imported into this container) is copied to the proxy and is used to make the LDAP secure connection.
Figure 11-1 General Page
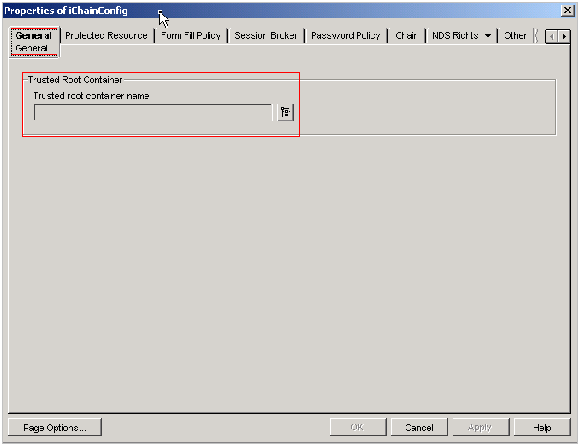
The Trusted Root Container is the eDirectory object you created and populated with certificates when setting up multiple certificate authorities. You must complete these steps before you can assign it to the proxy. For more information, see Configuring Multi CAs.