12.1 Encrypted Attributes
In eDirectory 8.8 and later, you can encrypt the attributes to protect data while they are stored on the disk. Encrypted attributes is a server-specific feature. You can use this feature in scenarios where you need to protect confidential data such as credit card numbers of bank customers.
When you encrypt an attribute, the value of the attribute is encoded. For example, you can encrypt an attribute empno stored in the DIB. If empno=1000, then the value of the attribute (1000), is not stored as clear text on the disk. You can read this encrypted value only when you access the directory over a secure channel.
All attributes in a schema can be enabled for encryption. However, we recommend you not to enable Common Name (CN) attribute for encryption and enable only the sensitive data for encryption. Refer to Achieving Complete Security While Encrypting Data before you decide on marking any attributes for encryption.
There is no limitation in accessing Public and Server readable encrypted attributes, this means that a client can access these attributes over clear text but you can mark these attributes for encryption at the DIB level. Enabling encryption on an attribute which is flagged [Public Read] in schema, does not prevent it from being accessed via non-secure methods.
Figure 12-1 Encrypted Attributes
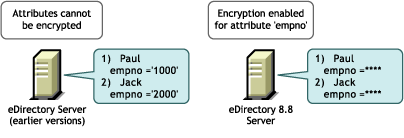
The data in eDirectory can be stored in any of the following ways:
-
In the Data Information Base (DIB) or database
-
As backup data
-
LDIF file
You can encrypt attributes by creating and applying encrypted attributes policies to the servers.
To encrypt the attributes, do the following using iManager:
-
Create and define an encrypted attribute policy.
-
Select the attributes for encryption.
-
Select the encryption scheme for the attributes.
Refer to Creating and Defining Encrypted Attributes Policies for more information.
-
-
Apply the encrypted attributes policy to a server.
Refer to Applying Encrypted Attributes Policies for more information.
You can also encrypt attributes through LDAP.
Refer to Managing Encrypted Attributes Policies Through LDAP for more information.
NOTE:Encrypted Attributes Policy assignment takes effect when Limber runs.
As a best practice, we recommend you to do the following:
-
Mark only sensitive attributes for encryption. Do not mark all attributes for encryption (for example, public or server readable attributes).
-
Use AES while marking an attribute for encryption as it is the strong encryption algorithm.
The rest of this section provides the following information:
12.1.1 Using Encryption Schemes
eDirectory 8.8 provides the highest level of security for an attribute by supporting the following encryption schemes:
-
Advanced Encryption Standard (AES)
-
Triple DES
-
Data Encryption Standard (DES)
You can select different encryption schemes for different attributes in a single encrypted attributes policy. For example, in an encrypted attributes policy EP1, you can select both AES as the encryption scheme for an attribute cubeno and Triple DES for an attribute empno. Refer to Creating and Defining Encrypted Attributes Policies for more information.
You can change the encryption scheme for an encrypted attribute by editing the encrypted attributes policy. You can also unencrypt an attribute that you have encrypted earlier. Refer to Editing Encrypted Attributes Policies for more information.
You can choose to have different encryption schemes in different servers of the replica ring. For example, an attribute might be enabled for encryption using AES on Server1, Triple DES on Server2 and no encryption scheme on Server3.
12.1.2 Managing Encrypted Attributes Policies
You can manage encryption of the attributes by creating and defining policies and applying them to servers.
You define an encrypted attributes policy by selecting the attributes for encryption and an encryption scheme.
Figure 12-2 Encrypting Attributes
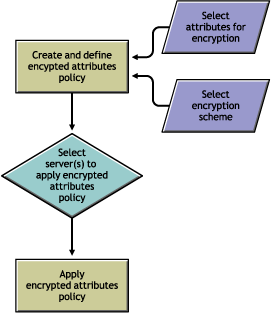
You can manage encrypted attributes policies using iManager. This section provides the following information:
Managing Encrypted Attributes Policies Through iManager
This section contains the following procedures:
If encrypted attributes are present in the eDirectory server, iManager behaves in the following manner:
-
Reading, listing, or modifying encrypted attributes is not allowed over clear text or secure channel.
-
An entry that has non-encrypted attributes is not allowed to read, list, or modify attributes through iManager over clear text or secure channel. This implies that the whole entry is blocked.
Creating and Defining Encrypted Attributes Policies
-
In NetIQ iManager, click the Roles and Tasks button
 .
.
-
Click eDirectory Encryption > Encryption Attributes.
-
In the Encrypted Attributes Policies Management Wizard, select Create, Edit and Assign policy.
-
Follow the instructions in the Encrypted Attributes Policies Management Wizard to create and define the policy.
Help is available throughout the wizard.
Editing Encrypted Attributes Policies
-
In NetIQ iManager, click the Roles and Tasks button
 .
.
-
Click eDirectory Encryption > Encryption Attributes.
-
In the Encrypted Attributes Policies Management Wizard, select Edit policy.
-
Follow the instructions in the Encrypted Attributes Policies Management Wizard to edit the policy.
Help is available throughout the wizard.
Applying Encrypted Attributes Policies
-
In NetIQ iManager, click the Roles and Tasks button
 .
.
-
Click eDirectory Encryption > Encryption Attributes.
-
In the Encrypted Attributes Policies Management Wizard, select Create, Edit and Assign policy.
-
Follow the instructions in the Encrypted Attributes Policies Management Wizard to apply the policy.
Help is available throughout the wizard.
Deleting Encrypted Attributes Policies
-
In NetIQ iManager, click the Roles and Tasks button
 .
.
-
Click eDirectory Encryption > Encryption Attributes.
-
In the Encrypted Attributes Policies Management Wizard, select Delete policies.
-
Follow the instructions in the Encrypted Attributes Policies Management Wizard to delete the policy.
Help is available throughout the wizard.
Managing Encrypted Attributes Policies Through LDAP
IMPORTANT:We strongly recommend you to use iManager for managing encrypted attributes and not LDAP.
This section contains the following procedures:
NOTE:You should specify the attribute and scheme pair while marking any attribute through LDIF for encryption and not the list of attributes and scheme. This is the current limitation with encrypted attributes.
Creating and Defining Encrypted Attributes Policies
-
Create an attribute encryption policy.
For example, the encrypted attributes policy is AE Policy- test-server, then
dn: cn=AE Policy - test-server, o=novell changetype: add objectClass: encryptionPolicy
-
Add the attrEncryptionDefinition attribute to the Policy object you created and mark the attributes for encryption.
For example, if the attribute name you want to encrypt is CRID then specify the encryption scheme and attribute name as mentioned below:
dn: cn=AE Policy - test-server, o=novell changetype: modify add: attrEncryptionDefinition attrEncryptionDefinition: aes$CRID
NOTE:Attribute name specifies the NDS name for the attribute. Many attributes in eDirectory have both an LDAP name and an NDS name. Here, specify the attribute name that requires the NDS name.
-
Add the attrEncryptionRequiresSecure attribute to the policy.
The value of this attribute specifies whether a secure channel is always necessary to access the encrypted attributes. The value 0 means that it is not always necessary. The value 1 means that it is always necessary.
For example:
dn: cn=AE Policy - test-server, o=novell changetype: modify add: attrEncryptionRequiresSecure attrEncryptionRequiresSecure: 0
-
Associate the policy with an NCP server.
For example, if the NCP server is test-server:
dn: cn=test-server, o=novell changetype: modify add: encryptionPolicyDN encryptionPolicyDN: cn=AE Policy - test-server, o=novell
Editing Encrypted Attributes Policies
The following LDIF file illustrates editing an encrypted attributes policy by changing the value of the attrEncryptionRequireSecure attribute:
dn: cn=AE Policy - test-server, o=novell changetype: modify replace: attrEncryptionRequiresSecure attrEncrytionRequiresSecure: 1
Applying Encrypted Attributes Policy
The following LDIF file illustrates applying an encrypted attributes policy AE Policy-test-server to a server test-server:
dn: cn=test-server, o=novell changetype: modify add: encryptionPolicyDN encryptionPolicyDN: cn=AE Policy - test-server, o=novell
Deleting Encrypted Attributes Policy
The following LDIF file illustrates deleting an encrypted attributes policy:
dn: cn=AE Policy - test-server, o=novell changetype: delete
NOTE:For more information on managing encrypted attributes through LDAP, see Using LDAP Tools on Linux and NetIQ Import Conversion Export Utility.
Copying the Encrypted Attributes Policies
In eDirectory 8.8 and later, you can copy the encrypted attributes policies to have identical configurations on many servers. The policies are stored as objects in eDirectory.
Refer to Copying Objects for step-by-step information on copying a Policy object using iManager.
Partition Operations
When you merge two partitions, the policies of the parent are retained for the resultant partition. When you split a partition, the child partition inherits the policy of the parent partition.
Recommendation: eDirectory stores several attributes for its own operations which should not be marked for encryption. If these attributes are marked for encryption, some of the eDirectory functionality will possibly be broken or it will not perform as expected.
The attributes that should not marked for encryption are:
-
federationBoundaryType
-
Volume
-
ACL
-
federationBoundary
-
member
-
federationControl
-
federationSearchPath
-
encryptionPolicyDN
-
indexDefinition
-
dgIdentity
-
dgAllowUnknown
-
agTimeout
-
Host Server
-
hostResourcePath
-
ndsPredicateState
-
ndsStatusExternalReference
-
ndsStausLimber
-
ndsStatusSchema
Though the list is not exhaustive, similar kind of attributes should not be marked for encryption.
12.1.3 Accessing the Encrypted Attributes
When you encrypt the attributes, you also protect the access to the encrypted attributes. This is because eDirectory 8.8 and later can restrict the access to the encrypted attributes over secure channel such as LDAP secure channel or NCP secure channel. However, only NetIQ internal customers can set up and use a secure NCP connection because the Dclient application, with which a secure NCP connection is created, is not available for public use.
You can also back up the encrypted attributes by using the Backup (ndsbackup) utility.
By default, the encrypted attributes can be accessed only through a secure channel.
However, if you want the clients to be able to access the encrypted attributes over clear text, then disable the Always Require Secure Channel option. For more information, refer to Enabling and Disabling Access to Encrypted Attributes Over Clear Text Channels.
Enabling and Disabling Access to Encrypted Attributes Over Clear Text Channels
You can enable or disable the access to encrypted attributes over clear text channels by enabling or disabling Always Require Secure Channel option (that is, the attrEncryptionRequireSecure attribute) using either iManager or LDAP.
This section contains the following information:
Enabling and Disabling Access to Encrypted Attributes Over Clear Text Channels Using iManager
To enable or disable the access to encrypted attributes over clear text channels using iManager, enable or disable Always Require Secure Channel in the Encrypted Attributes Policies Management Wizard while
Enabling and Disabling Access to Encrypted Attributes Over Clear Text Channels Using LDAP
To enable or disable access to encrypted attributes over clear text channels using LDAP, add the following attribute to the encrypted attributes policy:
attrEncryptionRequiresSecure
Setting this attribute to 0 makes a secure channel not always necessary, that is, you can access the encrypted attributes over a clear text channel. Setting it to 1 makes a secure channel always necessary, that is, you can access the encrypted attributes over a secure channel only.
Refer to Step 3 for more information.
12.1.4 Viewing the Encrypted Attributes
Viewing the attributes that are encrypted depends on whether you have enabled or disabled the Always Require Secure Channel option. This means whether you have specified that the encrypted attributes need a secure channel to access them or not.
Viewing Encrypted Attributes Using iManager
If Always Require Secure Channel is enabled, you cannot view the encrypted attributes. You get the error -6089, indicating that you need a secure channel to access the encrypted attributes.
If Always Require Secure Channel is disabled, you can see the encrypted attributes values in iManager.
For more information, refer to Browsing Objects in Your Tree.
Viewing Encrypted Attributes Using DSBrowse
If you have enabled the Always Require Secure Channel option, that is, if a secure channel is always required to access the encrypted attributes, you cannot view those attributes of the entry that are marked for encryption. However, you can view the other attributes of the entry that are not encrypted.
SNMP Traps
NDS® Value Events are blocked if you have specified that you always need a secure channel to access the encrypted attributes. Traps that are related to value events have value data as NULL and the result will be set to -6089, which indicates that you need a secure channel to get the encrypted attribute value. The following traps have the value data as NULL:
-
ndsAddValue
-
ndsDeleteValue
-
ndsDeleteAttribute
12.1.5 Encrypting and Decrypting Backup Data
While backing up data on a server that has attributes marked for encryption, you are prompted to provide a password to encrypt or decrypt backup data. The -E option in the Backup utility facilitates this. For more information, refer to the ndsbackup man page.
For more information on backing up your data, refer to Section 17.0, Backing Up and Restoring NetIQ eDirectory.
12.1.6 Cloning the DIB Fileset Containing Encrypted Attributes
While cloning, if the eDirectory database contains encrypted attributes in it, then the cloned DIB fileset will also have these attribute values encrypted. You need to set a password to secure the key used by eDirectory to encrypt the values in the cloned DIB fileset. When you place the cloned DIB fileset on another server, you will be asked to provide this password.
For more information, refer to Clone DIB Set.
12.1.7 Adding eDirectory 8.8 Servers to Replica Rings
You can add eDirectory 8.8 servers to replica rings irrespective of whether the attributes are marked for encryption on one or all the servers hosting the replica or whether Always Require Secure Channel is enabled or disabled.
For more information on adding eDirectory 8.8 server to the replica ring, refer to Adding a Replica.
12.1.8 Backward Compatibility
You need to change all eDirectory utilities like iManager, SNMP, DirXML® and NSureAudit to secure NCP™ to access encrypted attributes. Otherwise, you need to specify that a secure channel is not necessary to access the encrypted attributes. Refer to Enabling and Disabling Access to Encrypted Attributes Over Clear Text Channels for more information.
12.1.9 Migrating to Encrypted Attributes
When you upgrade to eDirectory 8.8 or later versions, you can encrypt the existing attributes by creating and defining encrypted attributes policies. For more information, refer to Managing Encrypted Attributes Policies.
12.1.10 Replicating the Encrypted Attributes
By default, encrypted replication is not enabled even if the server has the encrypted attributes. You need to enable encrypted replication for replicating the encrypted attributes securely. For configuring encrypted replication, refer to Encrypted Replication.