13.6 Using SSO to Salesforce on Mobile Devices
Salesforce now offers a combination of OAuth and SAML functionality to provide seamless SSO facilities not only for web browsers, but also desktop and mobile applications. By using OAuth to enable users to connect applications to their accounts, and leveraging SAML for the authentication of that connection, the single sign-on integration that was previously applicable only for the web browser can now service mobile applications.
The CloudAccess connector for Salesforce provides the necessary protocols and interfaces to the SAML and OAuth features of Salesforce. Single or multi-factor authentication can be used. The mobile device provides a standard browser interface to end users by using HTML. SSL/TLS is used for all appliance connections to protect user credentials and tokens.
13.6.1 Understanding the Mobile SSO Process
The following illustration provides a high-level overview of the mobile SSO to Salesforce process.
Figure 13-1 SSO to Mobile Salesforce Process
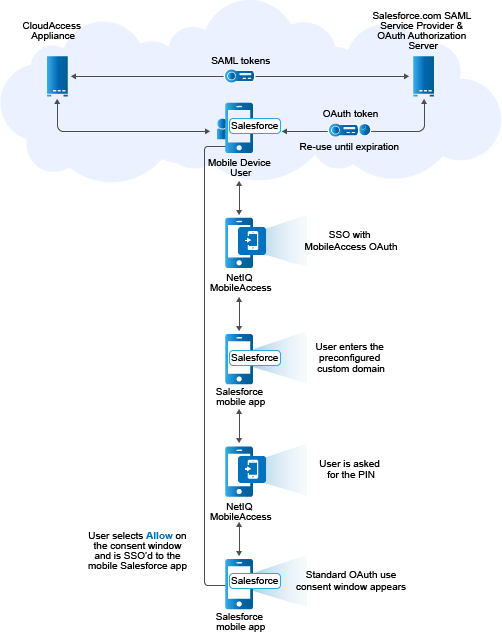
From the CloudAccess administrator’s perspective, the process is as follows:
-
The CloudAccess administrator sets up a SAML trust relationship between the CloudAccess appliance and the Salesforce service to provide user authentication and SAML tokens.
-
The end user authenticates with the CloudAccess appliance to obtain a SAML token and send it to the Salesforce.com server.
-
The Salesforce.com server accepts a valid SAML token from CloudAccess and issues an OAuth token for the mobile device.
-
The Salesforce native app stores and uses an OAuth token to access Salesforce.com services. The token is reused for future sessions, so the user does not have to re-enter credentials as long as the token has not expired.
From the user’s perspective, the process is as follows:
-
The user installs and sets up the mobile Salesforce app on a supported mobile device.
-
The user installs the NetIQ MobileAccess app on a supported mobile device.
-
The user opens the Salesforce mobile app on the device and enters the preconfigured custom domain.
-
The user is redirected to the NetIQ MobileAccess app and, if required, is asked for the PIN.
-
The user is redirected back to the Salesforce app and the standard OAuth use consent window appears.
-
The user selects Allow on the consent window and is SSO’d to the mobile Salesforce app. The user does not have to re-enter credentials until the OAuth session token expires.
-
When the user logs out of the mobile Salesforce app, the user sees the Salesforce.com login page.
NOTE:If the user does not have the MobileAccess app installed on the device (or if it was previously installed and then deleted), instead of being automatically authenticated, a NetIQ MobileAccess login screen appears in step 4 and the user must enter credentials.
13.6.2 Requirements for Mobile SSO to Salesforce
The following requirements must be met to enable SSO to Salesforce on mobile devices:
-
When you complete the connector configuration at Salesforce to allow single sign-on for users, you must configure a custom domain at Salesforce and provide the custom domain URL to users.
For more information, see Section 13.3, Configuring the Connector for Salesforce.
-
When you configure the connector for Salesforce in CloudAccess, you may create an appmark specifically for single sign-on to the mobile Salesforce app, selecting Native application from the list of Launch with options.
For more information, see Section 5.0, Configuring Appmarks for Connectors.
-
SAML SSO works on mobile devices only if the NetIQ MobileAccess app is also installed and configured on the device. Without MobileAccess installed on mobile devices, only delegated authentication using SAML is available.