3.0 Configuring Logon Filter
Logon Filter is a component that you must install on the Domain Controllers. It allows to automatically update group membership if you login with Advanced Authentication Windows Client. The Logon Filter can be used to forbid logon of users without the Advanced Authentication Windows Client or to delegate specific permissions when user uses a specific chain.
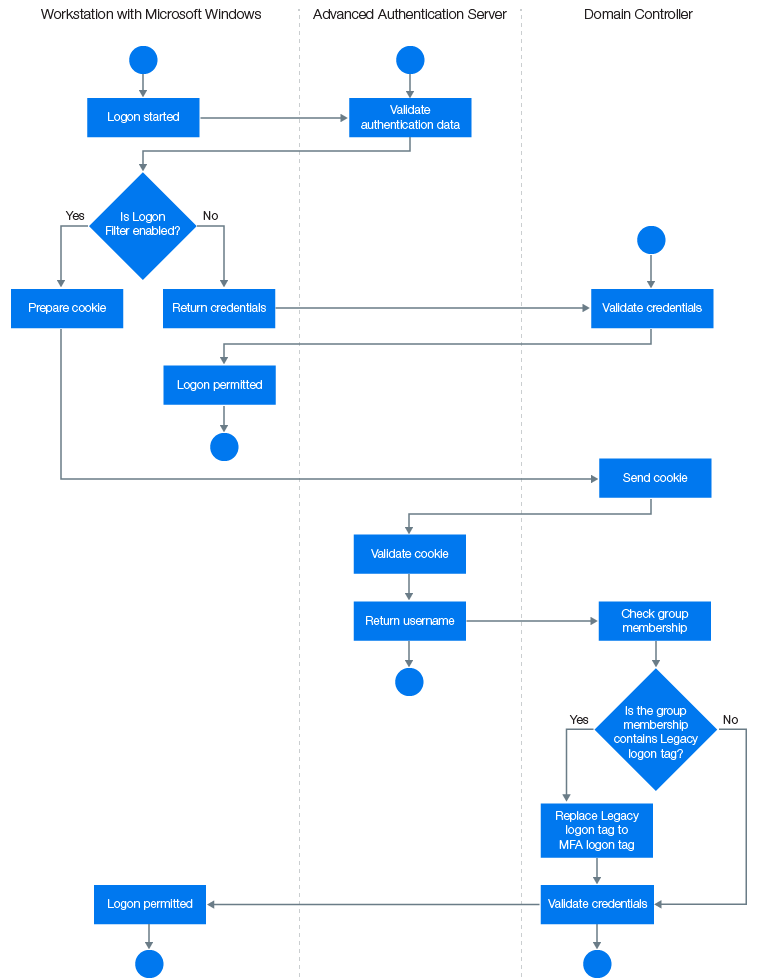
The following diagram illustrates the architecture of the Logon Filter.
Perform the following steps to configure the Logon Filter:
-
Install the Advanced Authentication Logon Filter component on all the Domain Controllers.
-
Enable Logon Filter through the Advanced Authentication Administration portal Policies > Logon filter for AD.
-
Create the following two groups in Active Directory:
-
Legacy logon: Add all users to the group (you can add the Domain Users group to its members).
-
MFA logon: This group must be an empty group.
You can use any names for the groups.
-
-
In the Advanced Authentication Administration portal Repositories section, specify a used Active Directory repository.
-
Expand the Advanced settings.
-
Point Legacy logon tag to the Legacy logon group and MFA logon tag to the MFA logon group.
NOTE:Legacy logon tag must point to a group in the Active Directory that must include all the users. It should be a custom group. The built-in groups like Domain Users are not supported. The users can be members of the group directly or you can add another custom group with users to the group. MFA logon tag should point to an empty group in Active Directory.
When a user logs in to Windows and the Logon Filter is enabled, Advanced Authentication Windows Client prepares a cookie, which is sent to the Domain Controller, and then is validated on the Advanced Authentication server. After the validation, Advanced Authentication server returns a username to the Domain Controller that verifies the group membership. If the group membership contains Legacy logon tag, the group is replaced with an MFA logon tag.
-
You can configure MFA tags per chain. To do this, specify the MFA tags in the Advanced settings of the chain settings. For example, if you specify a Card users group from Active Directory in MFA tags for LDAP Password+Card chain, then the users who use the chain will be moved from the Legacy logon group to the Card users group.
-
Specify a Password in the Repository settings.
-
Click Save.
-
Ensure that Advanced Authentication Windows Client is installed on all the required workstations.
NOTE: During logon, a user with the NetIQ Windows Client installed will be automatically moved from a group pointed to the Legacy logon tag to a group pointed to the MFA logon tag.
The MFA tag does not work while connecting to Remote Desktop, if the user credentials were saved with Remember my credentials.
If you want to prevent users to login on all the workstations that do not have the Advanced Authentication Windows Client installed, configure the Microsoft policy Allow log on locally in the default Domain Policy or a custom GPO. This allows logon for only MFA logon group. The following procedure helps you to achieve this:
-
On a Domain Controller, open Group Policy Management Editor by entering gpmc.msc in the search box.
-
Double-click the name of the forest, double-click Domains, and then double-click the name of the domain in which you want to join a group.
-
Right-click Default Domain Policy, and then click Edit.
-
In the console tree, expand and navigate to Computer Configuration > Policies > WindowsSettings >Security Settings > Local Policies > User Rights Assignment.
-
In the right pane, double-click Allow Log on Locally.
-
Click Add User or Group.
-
Specify a group which is pointed in the MFA logon tag.
-
Click OK.
-
Click OK in the Allow log on locally > Properties dialog box.