4.5 Risk-based Authentication
Traditional password-based authentication systems have their own limitations at implementing security in an organization. Enhancing the strength of the password is inadequate to prevent security threats. Thus, there is a need to explore and apply better authentication techniques such as risk-based authentication.
Risk-based authentication provides context-aware access control that acts to balance the level of trust against risk. It enables organizations to perform the following actions:
-
Address access-related risks and improves user experience.
-
Validate risk of an access request at the run time and take appropriate actions, such as forcing an advanced authentication or denying access.
You can also assess risk in a federated setup with service providers such as Salesforce.com, SAP HR, and Oracle Financial with protocols such as SAML and WS Fed.
Access Gateway can also control access for a protected resource based on the risk score.
The following illustration depicts risk-based authentication process:
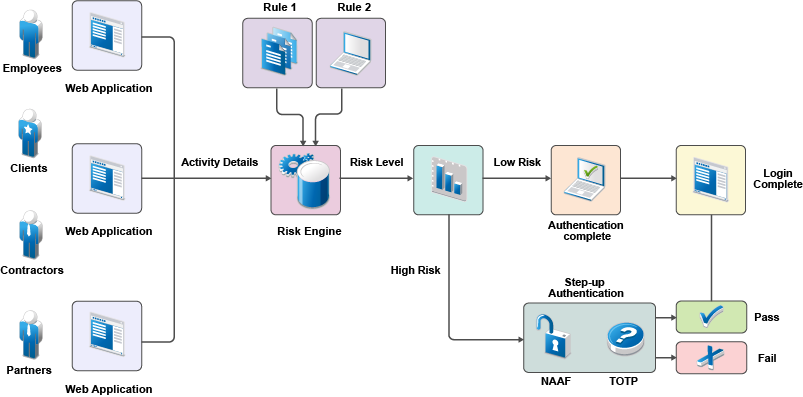
The following illustration depicts the risk-based authentication in a federated setup:
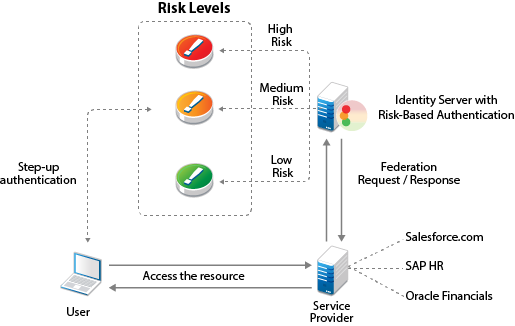
This section describes risk-based authentication concepts and how to configure it.