3.5.1 Configuring Attribute Sets
The attributes you specify on Identity Server are used in attribute requests and responses, depending on whether you are configuring a service provider (request) or identity provider (response). Attribute sets provide a common naming scheme for the exchange. For example, an attribute set can map an LDAP attribute such as givenName to the equivalent remote name used at the service provider, which might be firstName. These shared attributes can then be used for policy enforcement, user identification, and data injection.
Example 1: Attribute sets provide the centrally configurable means to map identity attributes between federation partners. When Access Manager Identity Server provides authenticated user information to a federated service provider such as Office 365, the attribute set determines what identity information is sent and available to Office 365 during and after authentication. The source of the identity data being sent can be the user's local LDAP directory or can be calculated dynamically. The identity data from external databases and secondary LDAP directories is achieved through Virtual Attributes. Virtual attributes are dynamically calculated attributes populated by the Attribute Retrieval and Transformation feature. See Section 3.5.8, User Attribute Retrieval and Transformation.
Example 2: You could have a web server application that requires a user’s e-mail address. You configure the web server to be a protected resource of Access Gateway, and you configure an Identity Injection policy to add the user’s email address to a custom HTTP header. When the user accesses the protected resource, the value of the email attribute is retrieved. However, if you create an attribute set with this attribute, then assign it to be sent with the authentication response of Embedded Service Provider of Access Gateway, the value is cached at authentication and is immediately available. If you have multiple attributes that you are using in policies, obtaining the values in one LDAP request at authentication time can reduce the amount of LDAP traffic to your user store.
You can define multiple attribute sets and assign them to different trusted relationships. You can also use the same attribute set for multiple trusted relationships.
To create and configure an attribute set:
-
Click Devices > Identity Server > Shared Settings > Attribute Sets > New.
-
Specify the following fields:
Set Name: Specify a name for identifying the attribute set.
Select set to use as template: Select an existing attribute set that you have created, which you can use as a template for the new set, or select None. To modify an existing attribute set, select that set as a template.
NOTE:If you require to add the LDAP attributes and the virtual attributes to an attribute set, select Supports WSTrust and OAuth.
For the OAuth scope, you can add LDAP attributes or only the virtual attributes that are LDAP attributes or are constants.
-
Click Next.
-
To add an attribute to the set, click New.
-
Specify the following fields:
Specify the attribute. Select from the following:
-
Local Attribute: Select an attribute from the list of all server profile, LDAP, shared secret attributes and virtual attributes. For example, you can select All Roles to use in role policies, which enables trusted providers to send role information in authentication assertions. Share secret attributes must be created before they can be added to an attribute set. For instructions, see Creating Shared Secret Names.
-
Constant: Specify a value that is constant for all users of this attribute set. The name of the attribute that is associated with this value is specified in the Remote Attribute field.
Remote Attribute: Specify the name of the attribute defined at the external provider. The text for this field is case sensitive.
-
A value is optional if you are mapping a local attribute. If you leave this field blank, the system sends an internal value that is recognized between Identity Servers.
For a SAML 1.1 and SAML 2.0 identity consumer (service provider), a name identifier received in an assertion is automatically given a remote attribute name of saml:NameIdentifier. This allows the name identifier to be mapped to a profile attribute that can then be used in policy definitions.
-
A value is required if you are mapping a constant.
An attribute set with a constant is usually set up when Identity Server is acting as an identity provider for a SAML or Liberty service provider. The name must match the attribute name that the service provider is using.
Remote namespace: Specify the namespace defined for the attribute by the remote system:
-
If you are defining an attribute set for LDAP, select none. If you want a service provider to accept any namespace specified by an identity provider, select none. If you want an identity provider to use a default namespace, select none. The urn:oasis:names:tc:SAML:1.0:assertion value is sent as the default.
-
If you are defining an attribute set for WS Federation, select the radio button next to the text box, then specify the following name in the text box.
http://schemas.xmlsoap.org/claims
-
If you want to specify a new namespace, select the radial button by the text box, then specify the name in the text box.
Remote format: Select one of the following formats:
-
unspecified: Indicates that the interpretation of the content is implementation-specific.
-
uri: Indicates that the interpretation of the content is application-specific.
-
basic: Indicates that the content conforms to the xs:Name format as defined for attribute profiles.
Attribute value encoding: Select one of the following encoding options:
-
Special characters encoded: Encodes only the special characters in the attribute value.
-
Not encoded: Does not encode the attribute value.
-
Entire value encoded: Encodes the entire attribute value.
-
-
Click OK.
The system displays the map settings on the Define Attributes page, as shown below:
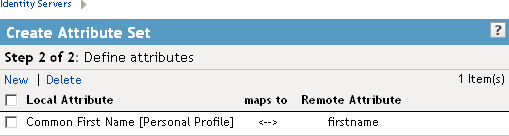
You can continue adding as many attributes as you need.
-
Click Finish after you created the map.
The system displays the map on the Attribute Sets page, as well as indicating whether it is in use by a provider.
-
(Conditional) To configure a provider to use the attribute set, see Section 3.9.6, Selecting Attributes for a Trusted Provider.